 Kerberos definition
Kerberos definition
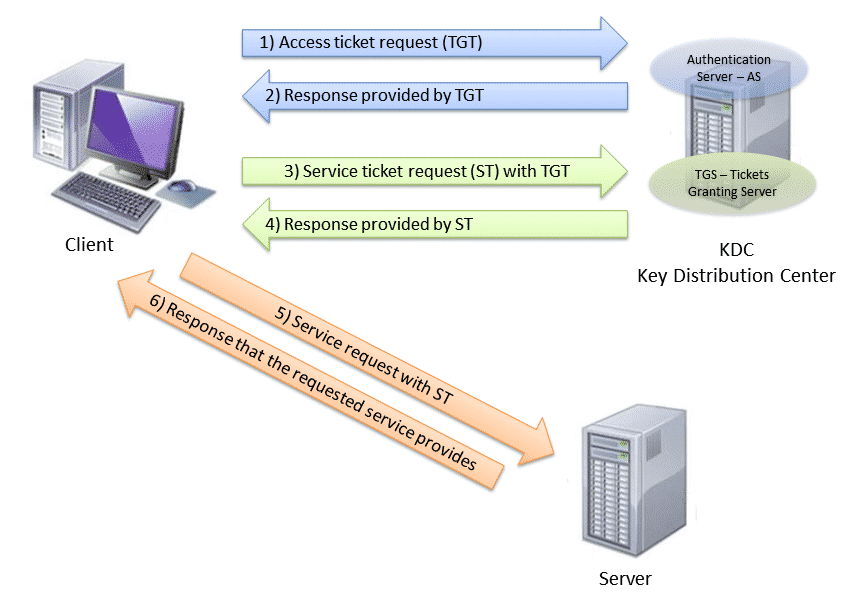
Kerberos is an authentication protocol that allows two computers to demonstrate their identity mutually in a secure way. Implemented on a client server architecture and works on the basis of tickets that serve to demonstrate the identity of the users.
Authentication between two computers is carried out using a trusted third party called the KDC-Key Distribution center, composed of two separate logical parts:
- AS – Authentication Server
- TGS – Ticket Granting Server.
Kerberos maintains a database of secret keys and each entity either clients or servers only have their secret key (known only by it and Kerberos). The privacy of this key is what makes it possible to prove the identity of each one. And for communication between two entities, Kerberos generates a session key, which they can use to secure their communications.
Architecture
Main concepts
Access Ticket (TGT)
Special ticket that allows the customer to obtain tickets for the rest of the tickets.
Are granted by the authentication Server (ACE)
Ticket (TGS)
Temporary tickets that allow to accredit a particular service. Examples of services: FTP, HDFS, HTTP,…
are awarded by ticket-granting server (TGS)
Kinit
Command that allows a master to already connect to get and cache the Access ticket (TGT).
Realm
A network that uses Kerberos, composed of one or more servers (known as KDCs) and a potential number of clients.
Main (main name)
The primary is the unique name of a user or service that you can authenticate by using Kerberos. A parent name is in the root @ REALM f[/instance]ormat. For a typical user, the root is the same as its logon ID. The instance is optional. If the principal has an instance, it will be separated from Root with a forward slash (“/”). An empty string (“”) is considered a valid instance (which differs from the default instance’s NULL value), but using it can be confusing. All the principals of a kingdom have their own key, which for users derives from their password or is generated randomly for services.
Keytab (key table)
A file that includes a decrypted list of “main” and its keys. Servers retrieve the keys they need from the keytab files instead of using Kinit. The default keytab file is/etc/krb5.keytab The KDC administration server, /usr/kerberos/sbin/kadmind, is the only service that uses another file (use: /var/kerberos/krb5kdc/kadm5.keytab).
How to generate a keytab in a cluster Hadoop?
Configuration files
- Core-site. XML: Describes the format and configuration for the core.
- HDFS-Site. XML: Describes the format and configuration for HDFS
- YARN-Site. XML: Describes the format and configuration for YAR.
- krb5. conf: Describes the format and settings for the Kerberos V5 library.
- KDC. conf: Describes the format and configuration for Kerberos V5 AS and KDC.
Source: Official website





0 Comments